5 Steps For Reducing Human Cyber Risk
October 13, 2022 | By: Stephen Boals
Cyber Security has come a long way over the past decade, and the technology aspect of the challenge is getting better and better each and every day. In fact, technical controls now prevent the majority of threats, 95%, from ever reaching their intended targets: our humans. But even with those protections in place, 82% of all data breaches involve human error. Organizations are struggling with how to train and adapt their users to the ever-changing social engineering threat, and the ever-increasing volume of email, messaging and voicemail attacks.
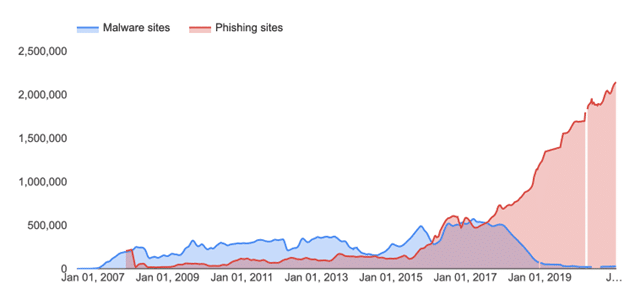
Human focused attacks continue to rise (Source: Google Safe Browsing Report)
Rote and repetitive training methods are creating a sense of fatigue, and Cyber Security teams are looking for new and innovative ways to mitigate Human Cyber Risk. Here are 5 steps to Reducing Human Cyber Risk and building a culture of mindfulness.
cyberconIQ was founded with the knowledge that technical approaches to cybersecurity alone do not address these prevalent issues we face today. With years of research and development with financial industry leaders, Dr. James Norrie discovered that our foundational CYBERology™ approach – the intersection of cybersecurity and psychology – would improve security outcomes and would advance the risk and compliance culture within organizations world-wide. With proven results that are 8 – 10x more effective than generic training alternatives, cyberconIQ’s Human Defense Platform measurably reduces the risk of a human-factors cybersecurity breach or data leak.
1. Have a tool/model to assess individual risk styles. To start, you need a method and process to evaluate and assess at the individual level. This assessment and evaluation is key for the next 4 steps in the process. Organizations are made of all type of personalities, and it takes all of those to make an organization hum. But when it comes to Cyber Security and the response to threats, all humans have a different risk style. I liken it to 4 people in a room with 4 chairs and one big red button in the middle of the table. No one has any idea what the button does, but the odds are there is someone in the room that will just press it. Essentially, in Cybersecurity today you have 10, 100, 1000, 10000 people in that room. Do you know who will push? Who won’t push? Understanding those risk takers and rule breakers is key to understanding and mitigating risk. Here is more: Cyber Risk Assessment.
2. Quantify and know your total organizational human risk makeup. You have to know where you are before you know where you are going. If I ask the question: What is the contribution of humans to your overall cyber risk factor? Can you answer? Your human risk profile is a major contributor to the probability and cost of a Cyber Breach. But digging in and estimating these factors is mostly a guessing game without proper tools. Here are some key questions to ask:
• Does my industry have an impact on my human Cyber Risk?
• Does my industry attract certain personality traits that are more vulnerable than others?
• What affects my human risk factors and how can I create visibility into the problem?
• What type of models can I use to present human risk and justify programs to mitigate?
Having this data at your fingertips as you plan and implement new controls can help you not only quantify the human risk factor, but also judge the cost-effectiveness of new controls and programs. Read more on quantifying human Cyber Risk.
3. Don’t create awareness, create mindfulness. The “awareness” in security awareness training is fleeting and creates a snapshot, content focused state of mind. It is maximized when your users complete training, and wanes very quickly, typically within <X> days. We call this the mind-full approach. Train the security threat right out of your employees by filling their minds with every bit of content you can scrounge up. But what happens when that Day Zero, new attack shows up? Something with a new pattern, a new meme? There is no awareness. There is no fallback to a programmed response or a “mind-full of content.” The key to reaching your organization’s minimum risk profile is to focus on creating a user population that is mindful and self-aware. One that can subconsciously STOP, and use a state of mindfulness to prevent today’s attacks, and successfully counter those in the future. Educate on context, not content. More on mindful, unique Security Awareness Training.
4. Remediate with a laser focus. Most organizations reward a user that fails a phishing test, with more content, and with the exact same training style. It’s assumed that the user training and retention is the problem, and that the failure can be trained right out of them with more and more volume, and more and more content. What if you knew psychologically WHY the user failed and educate them to know their own unique risks and vulnerability based on personality traits? What if you could user laser, pinpoint accuracy to remediate and create a positive outcome? Creating this self-awareness state is how best-in-class cybersecurity programs remediate their troublesome end users. Read about our focused Phishing Remediation Tool.
5. Culture starts at the top. Two of the most basic premises of leadership are: “Lead by example “ and “Take care of your people.” In most Cyber Security programs leadership goes through the same training as everyone else: the content curriculum. But in order to advance a culture of risk awareness and compliance, leaders need to be educated on not only the human side of the Cyber Security Challenge, but also how to handle remediation and the consequences of those that are not a cultural fit, or that pose extreme risk in an organization. Read about Cyber Security Training for Leaders.
For more about reducing Human Cyber Risk and our patented approach, contact us today.

