Quantification and Mitigation of Human Cyber Risk - A CISO’s Strategic Guide
October 9, 2023 | By: Dr. James Norrie
A playbook for reducing human cyber risk
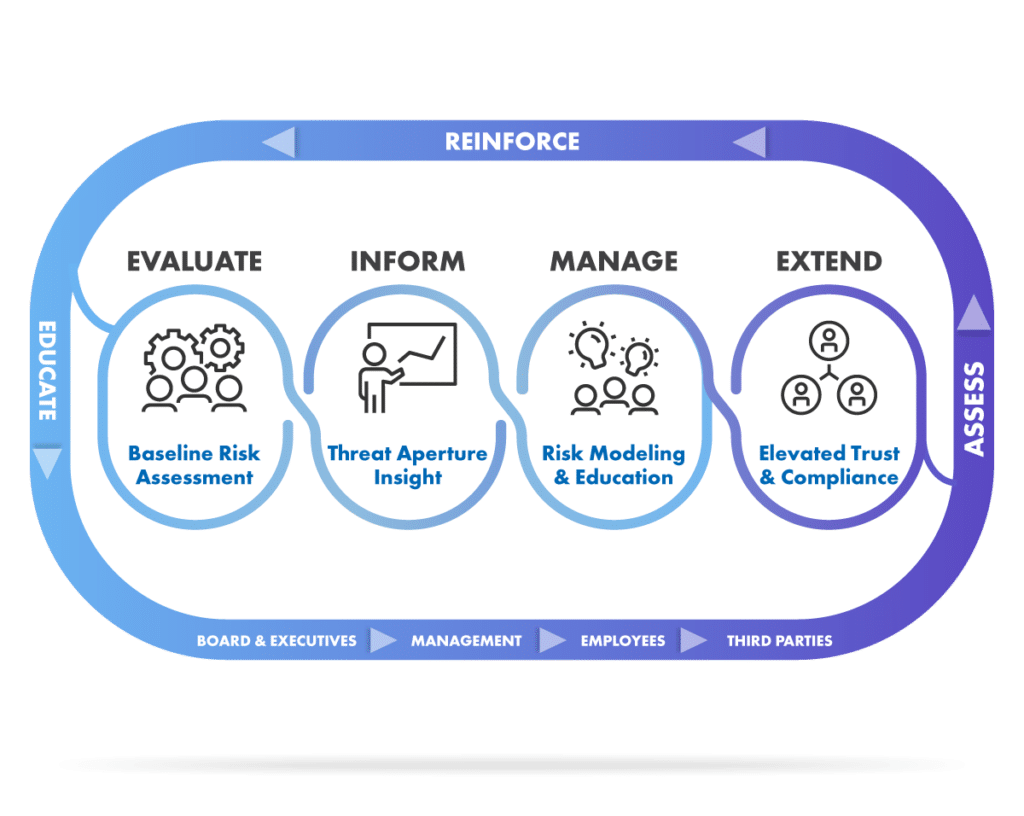
In today’s fast-paced cybersecurity landscape, Chief Information Security Officers (CISOs) and GRC leaders should be the vanguards of both technological control advancement and human risk behavior within organizations. Striking a balance between rapid tech innovation and the seemingly unpredictable nature of human actions presents a profound challenge. How does a seasoned CISO not only measure this dual-faceted risk but also construct strategies that are effective, forward-looking, and comprehensive in their approach? Based on our relentless dedication to the human side of cybersecurity research and innovation, cyberconIQ is proud to introduce our holistic 4-phase methodology, created with the unique challenges and responsibilities of the CISO in mind.
1. Evaluate: A Fusion of Analysis and Precision with myQ and Enterprise360
A CISO’s role isn’t limited to mere observation; it requires intricate analysis, understanding, and action. The myQ instrument, a cornerstone of our methodology and patent, offers a detailed breakdown that goes beyond surface metrics. It maps individual risk styles to specific cybersecurity vulnerabilities, enabling a CISO to discern distinct behavioral vulnerabilities at the individual, departmental, and organizational levels. This detailed mapping ensures a comprehensive understanding of potential gaps in cybersecurity posture, preparing the ground for interventions that are both targeted and effective. Combined with our Enterprise360 Analysis, CISOs are provided with a holistic evaluation of their organization’s technical and institutional debt.
2. Inform: The Power of Strategic Decision Making with 360 Analyses
In the boardrooms, numbers speak, but actionable insights resonate louder. With every decision resting on a precarious balance of risk and reward, Cyber360, Data360, and Insider360 analyses and cybermetrIQs tool emerge as invaluable assets. Offering a nuanced ROI analysis, focused squarely on both the human elements and over 100 data points, as well as a researched set of impactful indicators of cybersecurity maturity as defined by well-accepted frameworks (i.e. NIST, CIS, ISOx). With these tools, CISOs not only glean insights that drive decision-making but also possess the ammunition to underline the financial and strategic import of human-centric cybersecurity initiatives to key stakeholders, management, and board members. This has become critical for public companies subject to the new SEC cybersecurity incident reporting requirements.
3. Manage: Evolving Beyond Conventional Training Paradigms
One of the greatest misconceptions in cybersecurity is that a uniform training approach is universally effective. At cyberconIQ, we recognize the diversity of human behavior and vulnerabilities and advocate for a more personalized and customized training approach to reduce human cyber risk programmatically and predictably. By adapting to individual risk styles, this phase ensures that every member of the organization, regardless of their role or seniority, undergoes a learning journey tailored to their unique profile. This not only bolsters the effectiveness of training but turns each employee into a proactive participant in the organization’s cybersecurity defense. Your employees are now part of the solution and not part of the problem.
4. Extend: Reinforcing the External Frontiers of Security & Compliance
The modern business world isn’t an isolated entity. It’s a vast, interconnected web of vendors, partners, and regulators. As CISOs analyze their attack surface, they recognize that internal security measures, no matter how robust, can be rendered moot if external entities present vulnerabilities and vectors to compromise. The ‘Extend’ phase, therefore, is not just an add-on but a necessity and a growing concern in the age of AI and sophisticated, layered attacks. It meticulously evaluates third-party risk, ensuring that every entity connected to the organization is aligned with its security standards and focus. Furthermore, the inclusion of Regulatory 8K and 10K filing support and resources ensures that you maintain compliance with the growing regulatory changes.
The Conclusion: Adapt Your Program and Demonstrably Reduce Human Cyber Risk
The intricate dance between technology and human behavior in the realm of cybersecurity demands a guide that’s both comprehensive and adaptive. cyberconIQ’s advisory services expertise in human risk factors and our 4-phase approach, crafted with the nuances of a CISO’s role in mind, offers more than a toolkit—it presents a detailed map, strategic waypoints, and a vision for the future. It’s an invitation for CISOs to transform the often-perceived vulnerability of the human element into a fortified bastion of defense and vigilance.
cyberconIQ stands at the crossroads of innovation and practicality, dedicated to aiding CISOs in their mission to safeguard both data and people. If you’re ready to delve deeper into our patented and proven methodologies, discuss potential collaborations, or simply engage in a dialogue on the future of cybersecurity, please contact us.