New SEC Cybersecurity Reporting Rules - Moving Beyond the Checkbox
September 19, 2023 | Stephen Boals
Why Mitigating Is Better than Litigating in this New Regulatory Environment?
New SEC cybersecurity reporting guidelines imposed come without firm guidance on compliance. Sound familiar? Boards, CEO’s, CISO’s and others must now strive to quickly identify ways to enhance visible compliance efforts to avoid becoming an early test case who is litigated for the benefit of others learning what is really expected to close gaps. Under this scenario, here are three specific ways your organization can move to meet the intent of these new guidelines with a proven, patented solution that is easy to launch and implement before the Dec 15th deadline.
What Are You Doing to Remediate Your Serial Phishing Failure Users?
In light of the escalating scrutiny and enforcement threats facing public companies under these new guidelines, the Securities and Exchange Commission (SEC) has moved decisively to impose more stringent cybersecurity incident reporting rules. This means effective mitigation is more important than ever to avoid a reportable material event. Since more than 80% of successful attacks involve the weakest link in the security chain – the human element – an immediate recommendation is to reduce or eliminate repeat phishing simulation failures. If not addressed, this persistent challenge will continue to haunt enterprises globally.
Not only are serial clickers a drain on valuable cyber resources, require tracking, follow-up, counseling, and so on but this group of employees also represents your most visible and persistent breach risk, waiting to be compromised and utilized by bad actors in social engineering attacks. Your future filings will be expected to address this gap.
Recommendation: Contact CyberconIQ us to understand how a single pass of myQ and phishFixIQ can remediate up to 95% of your serial ‘clicksters’ in a single pass of our innovative training in less than 20 minutes.
Unpacking the New SEC Strategy & Governance Reporting Rule
Before we delve further into the intricacies of mitigating human risk, it is pivotal to understand not just the new SEC cybersecurity reporting rules, but the annual filing requirements which entail going well beyond reporting incidents themselves. The new rules mandate comprehensive reporting of your overall cybersecurity strategy and its governance. The swift arrival of this comprehensive reporting requirement for most companies begins this next fiscal year making transparency and timeliness paramount.
This approach will demand organizations have a proactive stance against a wide range of existing and new cyber threats exposing CISOs, CEOs, and Board members to increased pressure to apply advanced cyber expertise, model cyber risk and cost impacts, require integration it into overall business risk, and manage and report new cyber risks and mitigating investments under these new SEC guidelines. These reports can then be reviewed by the regulator to establish those that are and are not doing enough to secure their organizations against cybersecurity threats when compared to peers.
Recommendation: Immediately refocus your internal efforts to use various existing standards and frameworks that confirm the actual maturity of your cybersecurity strategy and approve actions to mitigate, transfer or accept these risks within a pre-defined level of cybersecurity risk that you establish, report, and actively govern as a Board mandate.
Despite advancements in technology that improve our perimeter, the human factor remains a significant and growing risk vector. The “accidental insider” remains one of the biggest, and most unpredictable, cybersecurity threats for most organizations. The SEC knows this too. As the Achilles’ heel in most organizations, continued susceptibility of employees to phishing/smishing and vishing attempts requires additional internal attention still.
With each passing day as we approach the full implementation of these new guidelines in December, these risk factor continue to expand in importance, and are exacerbated by several additional factors in the threat landscape:
- Repeat Phishing Failures – Individuals falling prey to phishing attempts more than once pose a substantial risk, giving attackers multiple entries into the organization’s network.
- Sophistication of Attacks – Phishers constantly evolve their tactics, utilizing deep knowledge of human psychology to manipulate individuals into providing sensitive information.
- Availability of AI – The utilization of AI for information gathering lifelike interaction with target users and real-time attack adjustment has placed the advantage in the attacker’s court.
- Inadequate Behavioral Focus – Many organizations do not leverage human risk measurement instruments to understand their individual user risk styles, and departmental and organizational DNA when it comes to vulnerability on the social engineering side.
Creating a Cybersecurity 1st Culture
Perhaps the most important shift is the tone of these new regulations to actually focus on individual employee behavior and your collective culture. The SEC appears to be demanding not just that we measure activity undertaken to mitigate cybersecurity risk, but to measuring the success of improved risk outcomes that demonstrate that your efforts are specifically working and that you can prove how and why. Many organizations try and implement consequences for continue breaches of security rules through an internal employee performance management system.
This is an important step and demonstrates the seriousness of putting security first. However, this can also instill fear in your employees, especially for repeat phishing simulation or training failures. The notion of a “three strikes rule” advancing towards termination is often viewed as being necessary by the security team, but thwarted by various employee protections, human resources policies and the fact that failing employees are often of high value to the organization. So, what is your board and security team doing to instill positive changes in your security culture that drive voluntary compliance and enthusiastic support for security driven by confidence instead of fear? Because that is the only way to achieve a lasting internal culture change.
Navigating Human Vulnerabilities in Cybersecurity
Internal cyber security teams are often at a loss on how to handle people that just can’t resist the “click”. They become frustrated: What do we do next? Continue counseling? Escalate the behavior up their reporting chain? Do we retrain over and over and over with the same content hoping for a new result? That likely won’t work either. But, these users pose a serious financial, legal and compliance risk so our internal mitigation of this must improve.
Recommendation: Be more strategic about measuring and managing human factors risk.
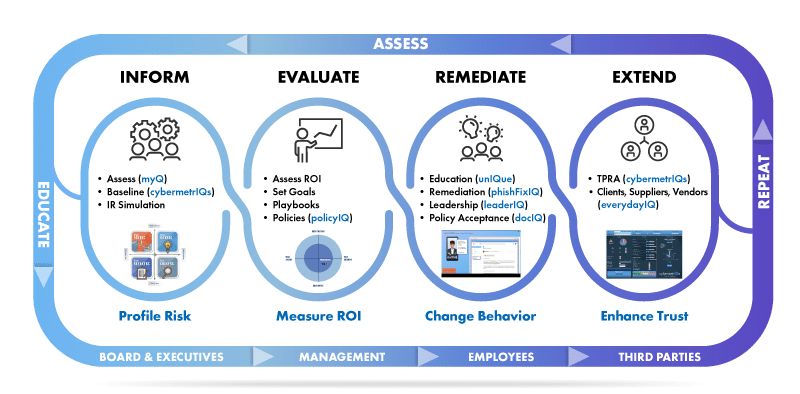
As we navigate the nuances of this substantial threat, it becomes evident that mitigating human risk is not merely advisable but vital, and public companies subjected to SEC rules can no longer ignore this high-risk area. Here, we outline a phased strategy to fortify the human element:
- Inform – Take steps for the organization to assess and baseline their human risk footprint or cyber DNA. This exercise will not only provide leadership with highly vulnerable areas but will also begin the journey for end users in understanding their personal risk-styles. This will lay the groundwork for a strengthened human defense posture and begin the remediation path for serial clickers. This step typically involves Incident Response exercises as well, to understand the people and process that will engage in incident analysis, especially around materiality of the incident.
- Evaluate – With the right human risk profile data, informed decision making can now take place. An ROI analysis can be made on remediation efforts, and probability of breach and incurred costs can be evaluated. Goals can be set; playbooks can be designed to create desired outcomes and policies can be constructed/enhanced.
- Remediate – Once you know your high-risk users and departments, you can provide personalized, advanced, and targeted training for their specific risk-style based on personality. This type of training is 10x more effective than standard content.
Note: Also use tailored training specifically for repeat phishing failures. Using the same content over and over will not produce different results for a percentage of your user base. - Extend – Your vendors, suppliers and consultants, and anyone else that has access to your resources, are a deep, deep risk to the organization. Does your third-party vendor assessment provide a statistical model that predicts probability of breach? Does it give a visual representation of human, process, and technical risk? Also, is there an opportunity to assess the individuals that will access your resources and identify possible human risk factors?
Conclusion: Human Risk – The Battleground of Today
As organizations grapple with the SEC’s determined focus on demanding that public companies, and those doing business with them create and implement a robust cybersecurity posture with the ability to point to evidence of a concerted efforts to thwart attacks and reduce breach risk.
The mandate to report incidents swiftly can only be effectively met when organizations stem the basic yet substantial tide of phishing attempts successful through repeated human error. The new rule, therefore, not only calls for adherence but beckons a transformation in organizational culture — one that pivots towards education, vigilance, and resilience.
In a landscape where the human risk is indeed the battleground of today, there is a need to fortify every individual, converting the weakest link into the strongest defense. The road ahead calls for a harmonized effort where technology meets humanity, crafting a shield impervious to the evolving cyber threats. It is time to revisit and reinvent our strategies, with the human element at the helm, steering organizations towards a safer, secure digital future.
Make the Right Choice – Choose CyberconIQ
In the intricate landscape of cybersecurity, the threats and challenges organizations face are ever-evolving. At cyberconIQ, we pride ourselves on understanding the nuanced dance between technology and the human element. Our patented methodology doesn’t just offer a solution—it presents a paradigm shift in how we perceive and tackle human-factor cyber vulnerabilities.
Every organization is unique, with its own set of challenges, goals, and employee dynamics. Recognizing this, our approach is tailored to address the individual needs, ensuring that the solutions provided are both relevant and effective. By integrating our innovative strategies, your organization isn’t just adopting a tool, but rather embedding a culture of cybersecurity awareness and resilience. Click here and dive in for a thorough exploration of all we offer and gain a richer understanding of our approach through our online platform. However, if you’re looking for insights specifically tailored to your organization’s unique landscape, we’re just a click away. Reach out to us for a personalized, complimentary consultation. Let’s collaboratively chart the path to a secure, digitally empowered future!
Want more in-depth recommendations? Read our recent White Paper on this topic here.